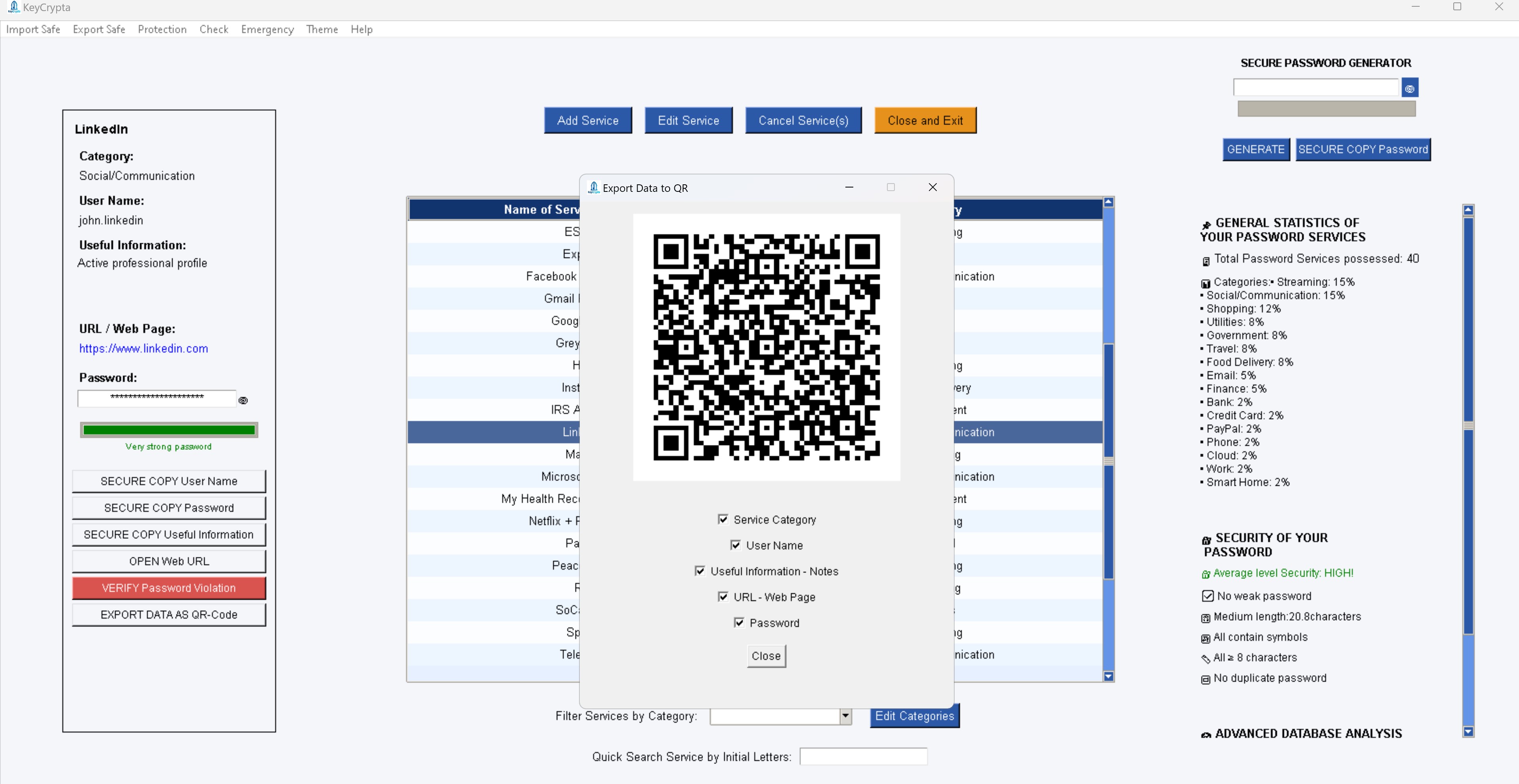
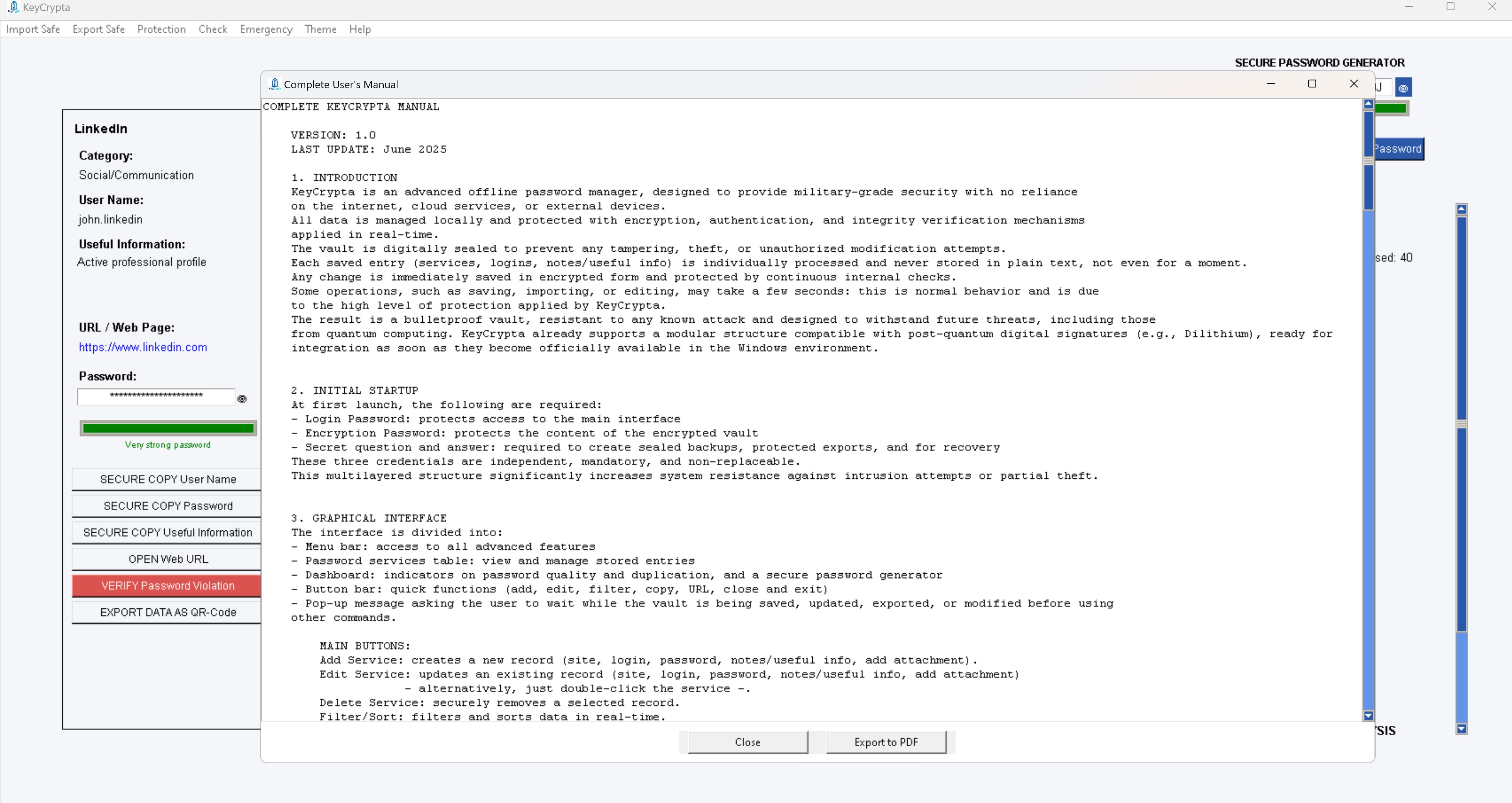
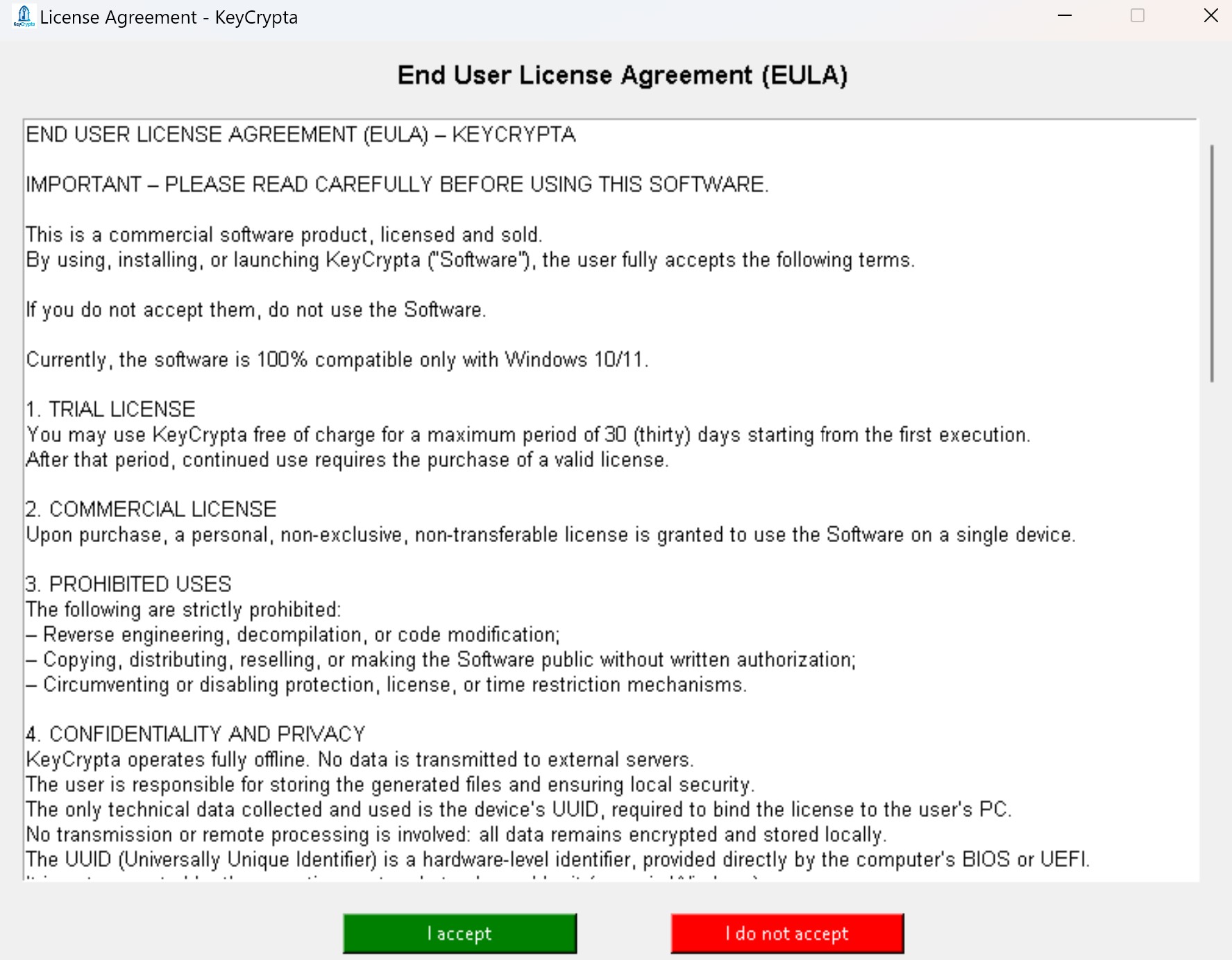
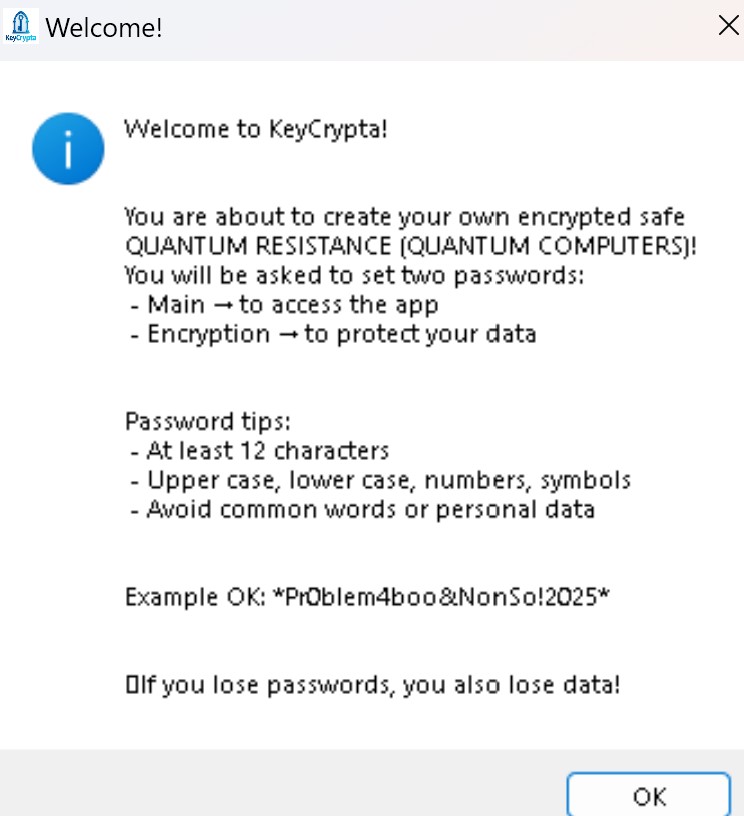
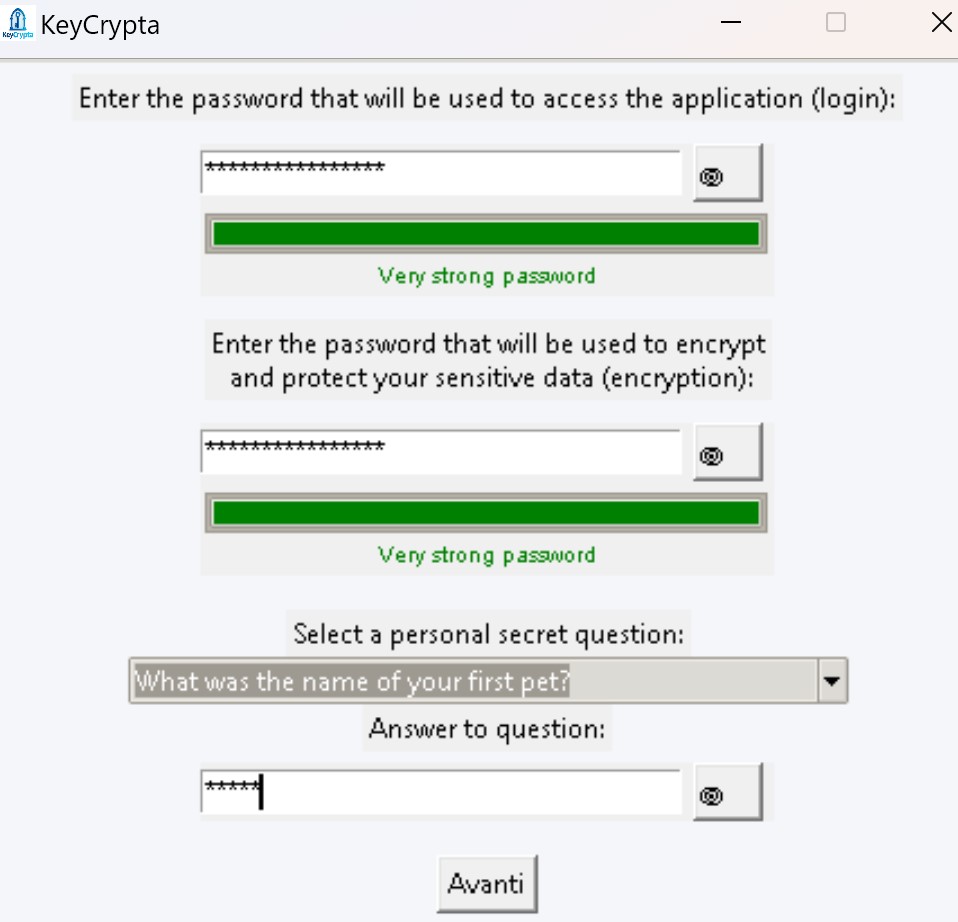
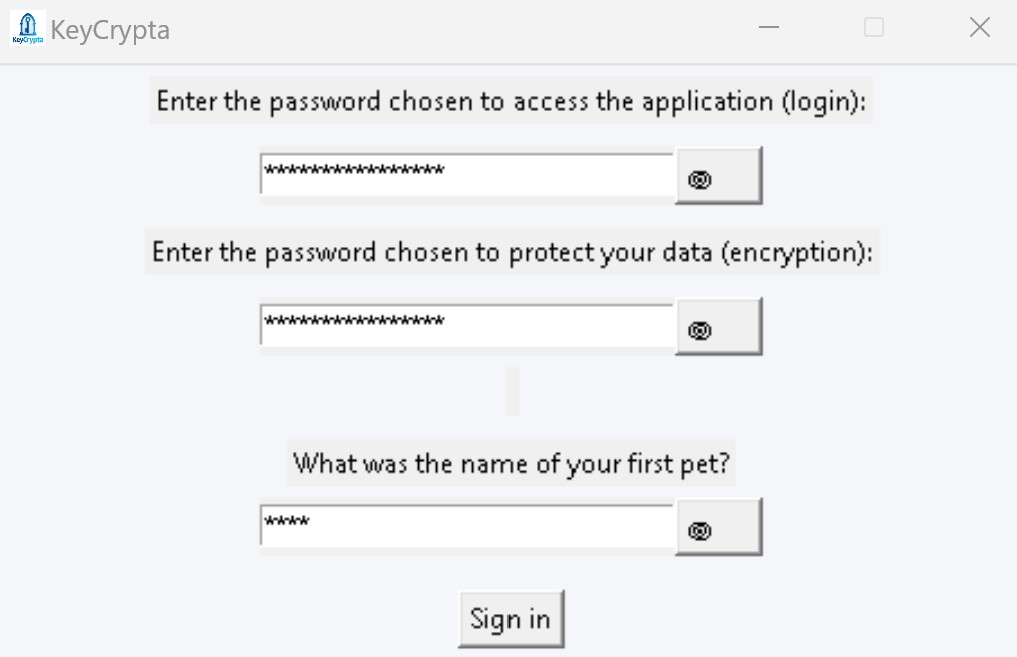
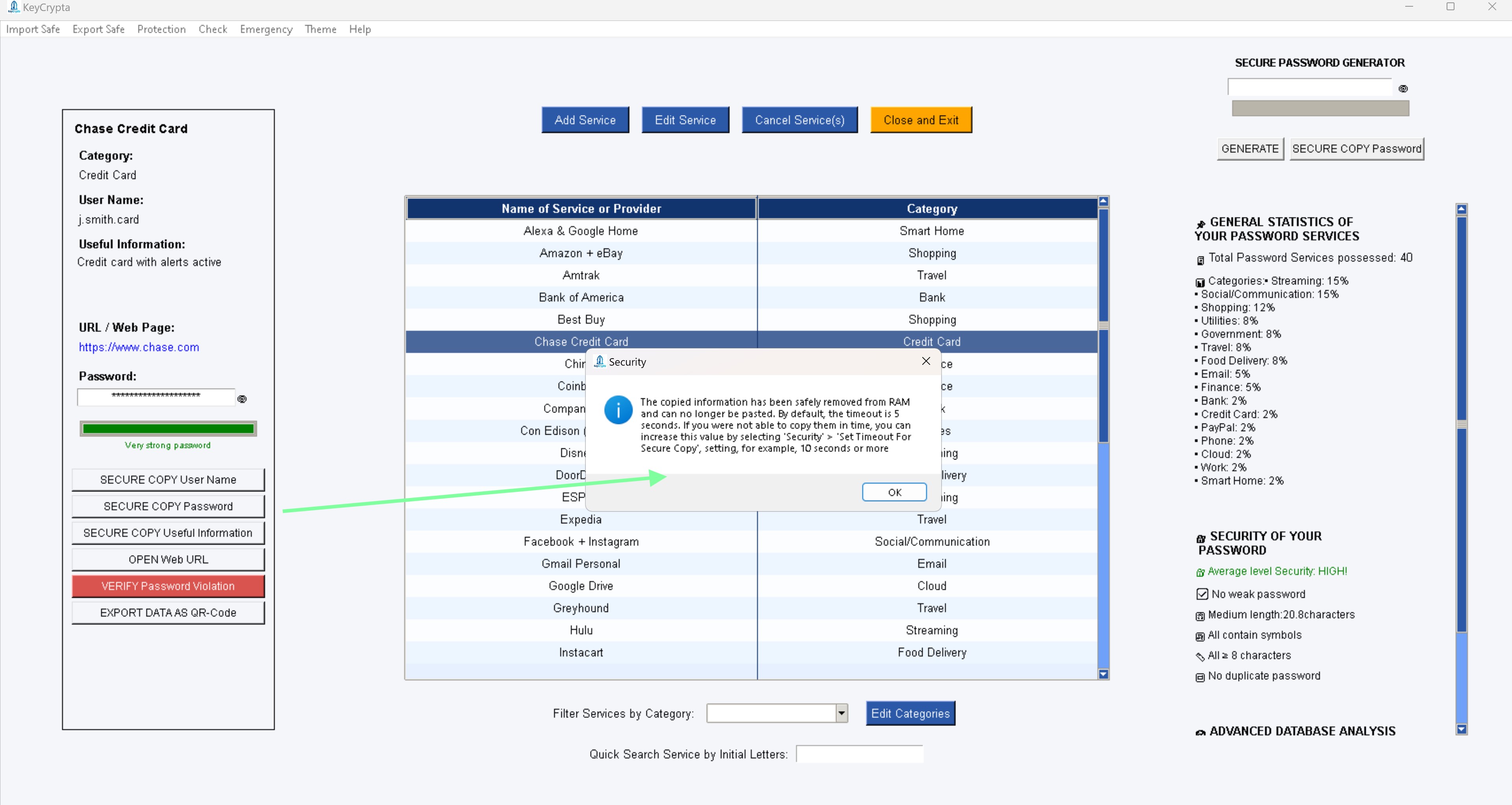
To activate KeyCrypta get your license NOW!
As stated in EULA point 5, KeyCrypta works fully offline.
The only data used is the local device UUID. Generate it with the offline tool, paste it, then choose your plan and language.
Remember that with a single payment, you will receive two licenses, allowing you to run KeyCrypta on two different computers (for example, your personal and work machines).
Saving KeyCrypta on a USB drive ensures maximum flexibility while remaining completely offline.
Step 1: Get your UUID
Download and run this tool on each computer to generate its unique UUID.
Then copy the code from each computer and paste it into the field below.
If you have two computers, run it on both; if you have only one, run it on that one.
Otherwise, if you are an advanced user, instead of downloading the program that does it automatically with one click, you can get your PC’s UUID using Command Prompt (Win + R → type cmd → Enter) and typing wmic csproduct get UUID.
Alternatively, you can use PowerShell (Win + R → type powershell → Enter) and type (Get-CimInstance Win32_ComputerSystemProduct).UUID.
In both cases, a code will appear under the word UUID, and this is the code you must copy exactly, including letters and dashes, as your PC’s unique identifier, for example: 4C4C4544-0032-5710-8058-B6C04F563231.
Download UUID Generator